Introduction
On 18 March, 2022 HALO Network announced their partnership with Redruby DAO. According to a medium blog posted by HALO Network, Redruby DAO, claims inspiration by Taylor Swift, and declared they hoped to revolutionize philanthropy through blockchain technology. Redruby DAO claims that they also aspired to use the decentralized autonomous organization (DAO) approach to create a truly efficient philanthropic service.
The partnership between HALO Network and Redruby DAO, allows Redruby DAO to receive liquidity from HALO Network. HOSWAP, the HALO Networks main decentralized exchange (DEX) handles the liquidity provision, ensuring Redruby DAO gets access to liquidity based on the terms of their agreement.

On 4 October, 2022 at 3:04:02 PM +UTC, Redruby DAO was exploited by an unknown actor and lost approximately $91,020. Due to the lack of input validation of the withdrawer’s balance in the RRB staking contract, the exploiter was able to use an attack contract to bypass the sanity check. This allowed the exploiter to drain the RRB tokens from the staking contract and then ultimately selling them off to steal the funds.
Addresses
Exploiter:0x9a52daeb40b898b1af30c5c428243d4c827b18ad
Attack Contract:0x771f25e77d78be8f1a4f01efa43bae9ca559d9a8
Unverified Redruby DAO Token Contract: 0x4161557153cf56b10836b3f76f9b82561f23cb0c
Staking Contract:0x06d4a0dec3fa502d01ea7919f95ff3a7c3904c9d
Redruby DAO Old Token Contract on HOSWAP: 0xa8d22026119bC8A33941853614148Fda61971d4D
Attack Flow
-
On 4 October, at 03:04:02 PM +UTC, exploiter, 0x9a52d, which is funded by tornado.cash, creates attack contract 0x771f2.
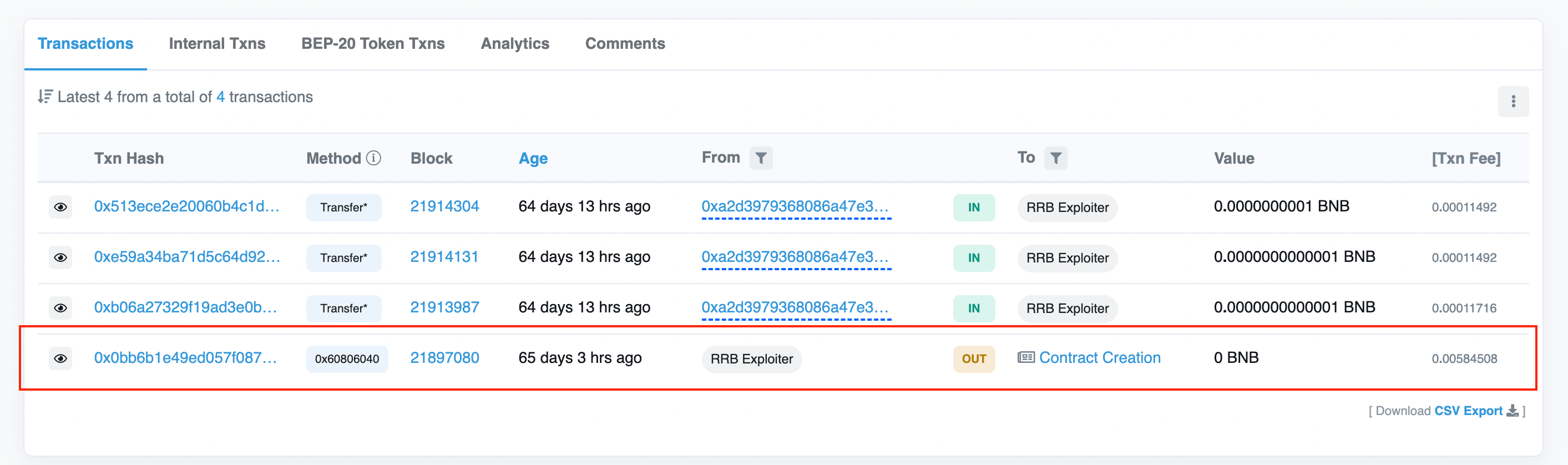
-
The exploiter contract 0x771 drained the contract 0x06d, via withdraw(0x2e1a7d4d) because of the design flaw in the staking contract.
-
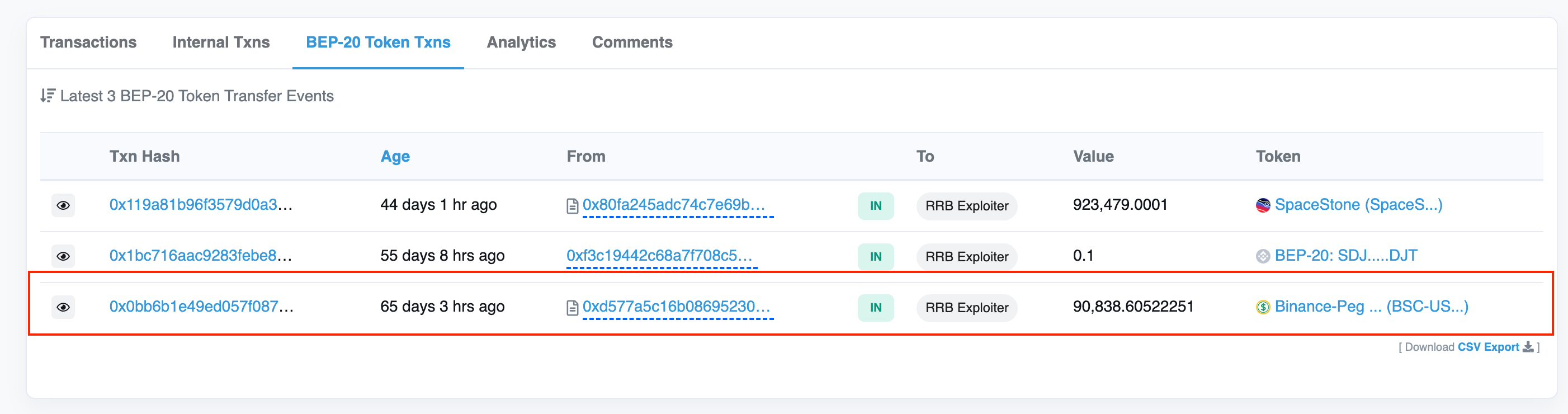
The exploiter sold the token via W3swap.
-
The exploiter contract transferred all BSC-USD to exploiter 0x9a52d.
Vulnerability
The withdraw() function in the contract lacks the validation of the withdrawer’s deposit balance. On line 77, the function only checks if the withdrawer’s deposit balance is nonnegative, which is always true.

Then, if the msg.sender is a contract, on line 88, the contract will transfer the provided amount of the tokens to the msg.sender.

Stolen Assets and Tracing
The total assets stolen from this exploit is $91,020. At the time of writing, the stolen assets remain in the exploiter’s wallet 0x9a52.
Conclusion
Although only $91,020 was taken, Redruby DAO is a great example as to why users should only interact with audited and verified smart contracts. The exploitable feature in the contract issue lay lied in the balance validation issue which would have been caught by an audit. Smart contract auditing can recognize and neutralize incidents before malicious actors can exploit and steal funds. Protect yourself and your assets by following @CertiKAlert on Twitter to stay up to date on all the latest Web3 security news, and visiting CertiK.com as part of your due diligence.
Do your own research and beware of scam tokens!





