TL;DR
On March 5, 2022, Bacon Protocol experienced an exploit via a flash loan attack for loss of nearly $1 million to the protocol. The exploit appears to result from the attacker taking advantage of a reentrancy issue within the lend() function of Bacon Protocol. Since the incident the project recognized the attack and reaudited contracts completely. Soon after they would rebrand as HOME Coin and recapture momentum.
Summary
Bacon Protocol was a decentralized mortgage lending protocol created using smart contract technology on the Ethereum blockchain. Bacon Protocol introduced a way for cryptocurrency wallet holders to hold a coin backed by mortgages similar to those used by banks, insurance companies, and governments. Bacon Protocol’s token, bHOME, was backed by liens against homes in the United States and grows based on payments made against those liens.
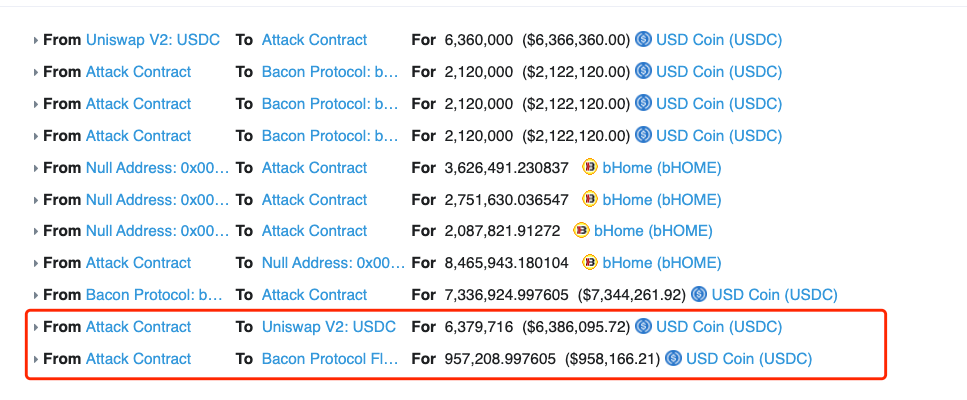
On March 5, 2022 at 12:46:23 PM +UTC, Bacon Protocol suffered a major incident causing a total loss approximately 957,209 USDC, which is about $959,123 in USD. The attacker (0x7c42f2) borrowed 6.36M USDC from Uniswap to lend to Bacon Protocol and receive bHome tokens as a reward. This process abused a potential reentrancy within the lend() function, allowing the attacker to receive far more bHome then intended. Afterward the hacker invokes redeem() to swap all bHome to USDC and repays the flash loan while receiving all profit back to the hacker address. Since the Bacon Protocol implementation contract was unverified, this complete attack vector can not be proved with confident assuredness.
The protocol announced the incident publicly via Twitter on the day of the attack stating that someone used reentrancy to claim more bHOME than intended and that most funds were already safely lent out against homes. The issue was caught quickly and the contract was patched. The team announced and immediate re-audit of the affected contract.
 Since the incident, it appears Bacon Protocol has dissolved and been rebranded. The original Twitter account @baconprotocol has been completely wiped. The Twitter primarily used today is @homecoinfinance and along with it comes their complete rebranding to HOME Coin. HOME Coin follows a similar design but offers investors the opportunity for consistent yield through a stablecoin backed by home mortgages.
Since the incident, it appears Bacon Protocol has dissolved and been rebranded. The original Twitter account @baconprotocol has been completely wiped. The Twitter primarily used today is @homecoinfinance and along with it comes their complete rebranding to HOME Coin. HOME Coin follows a similar design but offers investors the opportunity for consistent yield through a stablecoin backed by home mortgages.
Relevant Addresses
Bacon Protocol proxy contract address: https://etherscan.io/address/0xb8919522331c59f5c16bdfaa6a121a6e03a91f62
Bacon Protocol implementation contract address (unverified): https://etherscan.io/address/0x781ad73f140815763d9a4d4752daf9203361d07d
Hacker address: https://etherscan.io/address/0x7c42f2a7d9ad01294ecef9be1e38272c84607593
Hacker created attack contract (self-destructed): https://etherscan.io/address/0x580cac65c2620d194371ef29eb887a7d8dcc91bf
Attack Flow
- The attacker (0x7c42f2) borrowed 6,360,000 USDC to the Attack Contract (0x580cac) from Uniswap, a decentralized cryptocurrency exchange.
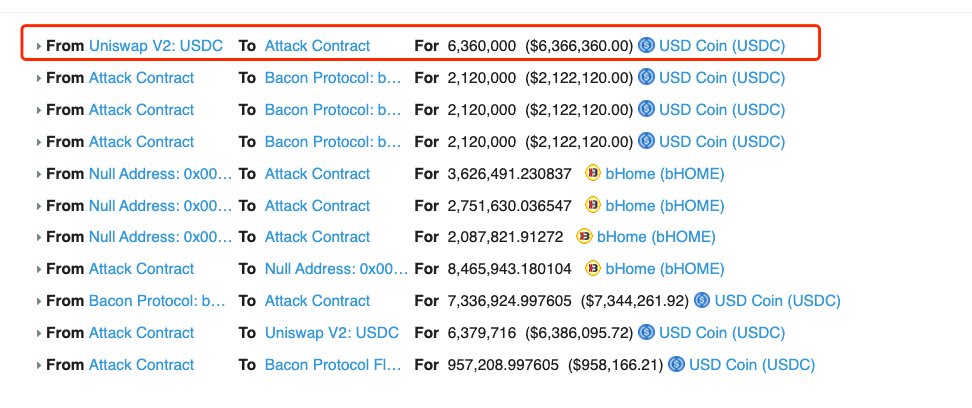
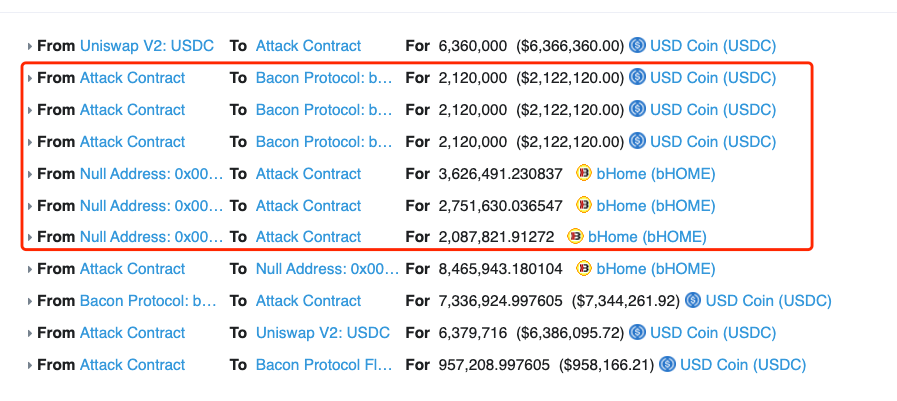
- The Attack Contract lent USDC to Bacon Protocol and got bHome as a reward. However, this action took advantage of a potential reentrancy issue in the lend() function of bacon protocol, thus allowing the attacker to get more bHome than deserved.
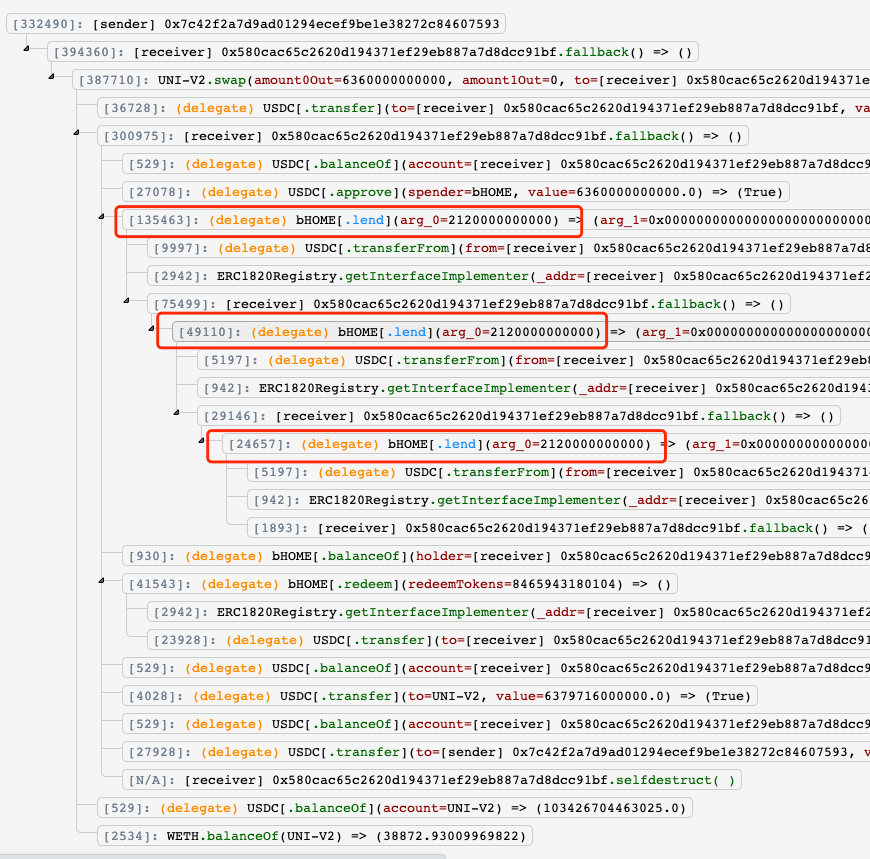
- Hacker calls redeem() to redeem all received bHome to USDC
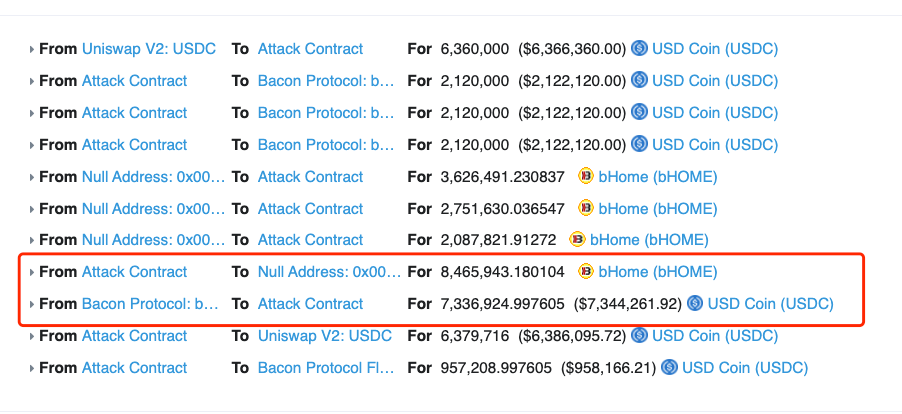
- Repaid the flash loan and transfer the profit to hacker’s address
 Attack Transaction:
https://etherscan.io/tx/0x7d2296bcb936aa5e2397ddf8ccba59f54a178c3901666b49291d880369dbcf31
Attack Transaction:
https://etherscan.io/tx/0x7d2296bcb936aa5e2397ddf8ccba59f54a178c3901666b49291d880369dbcf31
Contracts Vulnerability Analysis
Since the Bacon Protocol implementation contract address is unverified, we can only speculate the potential issue. After decompiling the lend() function of the Bacon Protocol contract, the following lines are made evident:
 Function tokensReceived() is the ERC777 interface which doubles as a hook that could be used to initialize the reentrancy issue.
Function tokensReceived() is the ERC777 interface which doubles as a hook that could be used to initialize the reentrancy issue.
Conclusion
The Bacon Protocol exploit highlights how destructive flash loan attacks can be to project growth. Over the course of the year we have seen flash loan attacks like this or the Beanstalk Farms incident, where irreparable damage is done to the protocol. Flash loans can have high severity and bring project momentum dead stop before they can capitalize on their product. With exceptional smart contract auditing, gaps and vulnerabilities can be recognized and subsequently neutralized before malicious actors can exploit. Get your project audited at CertiK.com today and send you project to the moon without turbulence!





 Attack Transaction:
Attack Transaction:


