TL;DR
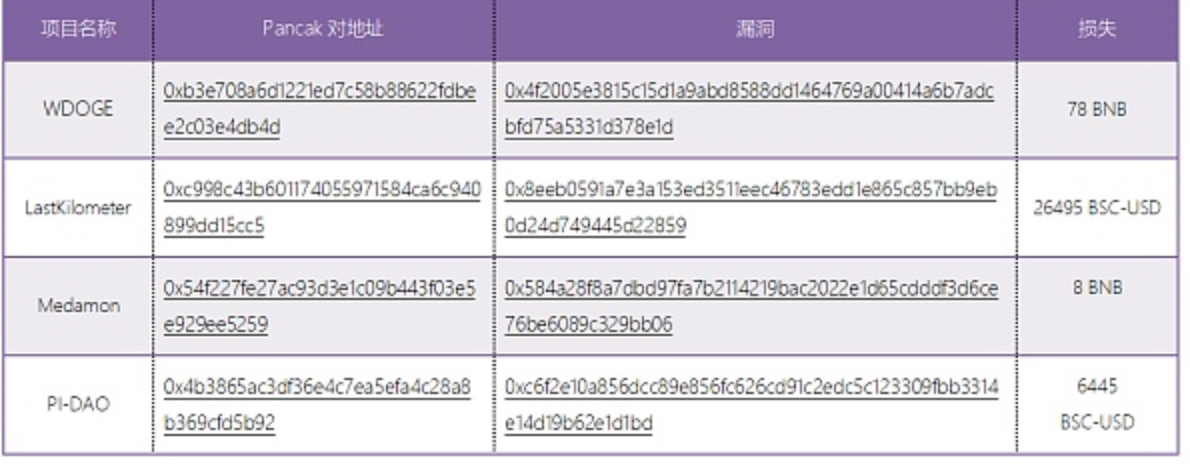
On April 25 2022, at 8:33 AM +UTC, the Wiener DOGE project was exploited, causing a loss of ~30, 000 USD. The attacker exploited the inconsistency between WDODGE’s charging mechanism and the exchange pool to launch the attack.
Event Summary
The root cause stemmed from the deflationary token contract, where the LP Pairs as sender were not excluded from the transfer fee. Therefore, the attacker was able to drain out the deflationary tokens within the LP Pairs, which caused the price imbalance of the pairs leading to a profit.
The hacker flashloaned 2,900 BNB, swapped 5,974,259,851,654 WDOGE tokens from the WDOGE and BNB transaction pairs, and then retransferred 4,979,446,261,701 tokens into the transaction pairs.
Transaction hash:
0x4f2…
Hacker address:
0x962…
Profited address:
0x46b…
Three other malicious exploits followed on the same day:
-
Last Kilometer project was exploited by a flash loan attack, resulting in a loss of US$26,495 (equivalent to about 170,000 RMB);
-
The Medamon project was exploited by a flash loan attack, resulting in a loss of $3,159 (equivalent to about 20,000 RMB).
-
The PI-DAO project was exploited by a flash loan attack, resulting in a loss of US$6,445 (equivalent to about 40,000 RMB).
The attackers and attack methods of this series of attacks are the same as Wiener DOGE that occurred earlier in the same day.
Attack Technical Analysis:
The attacker :
-
Took a flash loan of 2900 BNB;
-
Swapped 2900 BNB for 6 638 066 501 837 WDOGE
Status of LP:
-
WDOGE : 199 177 850 468
-
WBNB: 2 978
- Sent 5 974 259 851 654 WDOGE (some fees are taken from this amount) to the LP, the LP is now in imbalance since there are more WDOGE than BNB.
Status of LP :
-
WDOGE : 5 178 624 112 169
-
WBNB : 2 978
- Called the skim() function to retrieve 4 979 446 261 701 WDOGE;
When the LP sends tokens, it also has to pay the fees, which will decrease the amount of WDOGE within the LP. Since a large amount of WDOGE was sent by the attacker before calling skim(), the LP will pay a large fee. This operation emptied the amount of WDOGE within the LP.
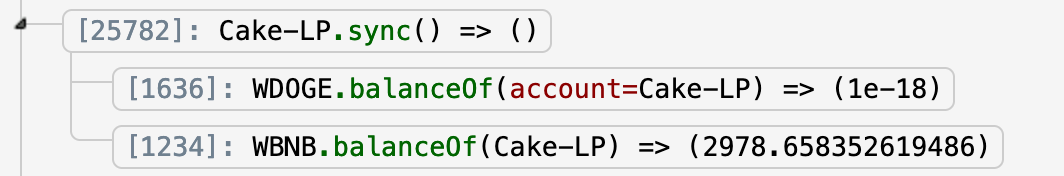
The attacker also called the sync() function to update the values in reserves within the LP. There are now few WDOGE and 2 978 BNB, making the price of WDOGE very expensive compared to WBNB.
- Swapped his remaining WDOGE to retrieve the 2 978 BNB, repaid the flash loan and made a profit of 78 BNB.
Contracts Vulnerability Analysis
When a user (or a LP) transfers a given amount of WDOGE; in addition to the fees, 4% of the amount of tokens will be burnt.
Therefore, if the LP sends 100 WDOGE, its balance will decrease by 104 WDOGE.
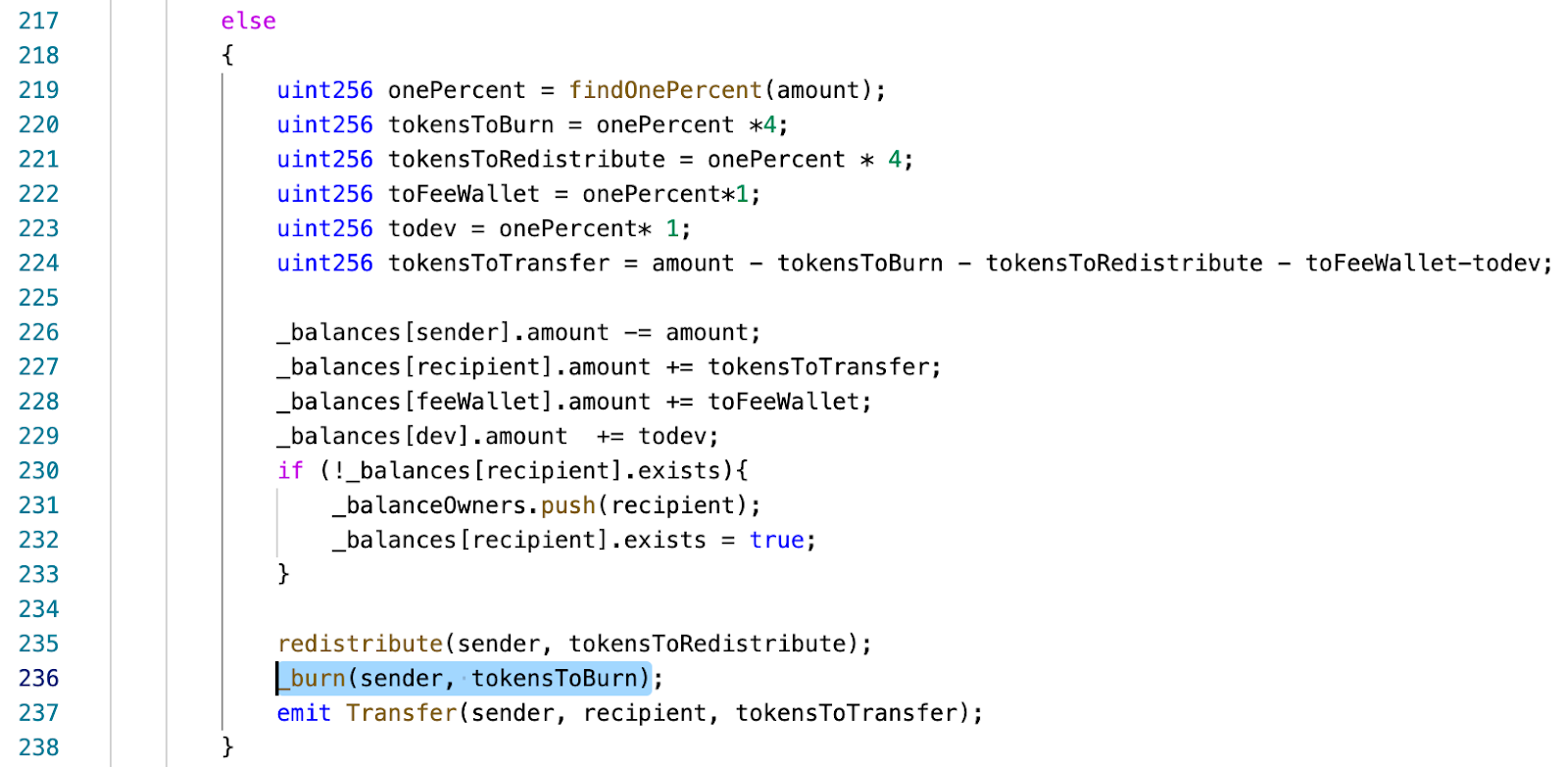
The LP should be excluded from fees and tokens burns.
Profit and assets tracing
78 BNB or 30 000 USD were loss in the transaction that can be found: https://bscscan.com/address/0xbdf…
Conclusion:
The hacker exploited the deflationary nature of the tokens by having the transaction pair burn off a portion of the transaction pair tokens during the skim, corrupting the calculation of the k-value. The vulnerability could’ve been found if both tokens and LP audited the contract. If only token contracts are audited then the switch system will be regarded as an external dependency.



